Are you curious how DxEnterprise clustering software actually delivers industry-leading SQL Server high availability (HA), cost savings, and simplified infrastructure management?
Then you’ve come to the right place.
In this blog we’ll be taking a detailed look at the patented core technologies that make up our DxEnterprise high availability solution, InstanceMobility® and Vhosts. We’ll provide an in-depth explanation on how:
- Instance-level abstraction makes it possible for our customers to achieve an 8-15x reduction in OSes under management
- Unmatched flexibility helps our customers reduce SQL Server and Windows Server licensing costs by 30-60% while remaining totally Microsoft-compliant
- Failover automation and simplified modernization practices unlock nearest-to-zero unplanned AND planned downtime for DH2i customers
InstanceMobility & Vhosts: DH2i’s Ultimate SQL Server HA Enablers
When it comes to unpacking the DH2i software componentry—the “secret sauce” if you will—that makes everything else possible from the ground up, the only place you can start is InstanceMobility.
InstanceMobility is a proprietary approach to workload portability. Since the early 2010s, global enterprises have relied on this technology for instance-level high availability that spans physical, virtual, and cloud environments.
InstanceMobility uses an extremely lightweight, agile abstraction technology that allows you to:
- Move SQL Server instances, containers, services, or file shares between any hosts, anytime, anywhere
- Eliminate infrastructure lock-in by intelligently decoupling workloads from the underlying OS (Windows/Linux) and infrastructure (bare-metal/virtual/cloud)
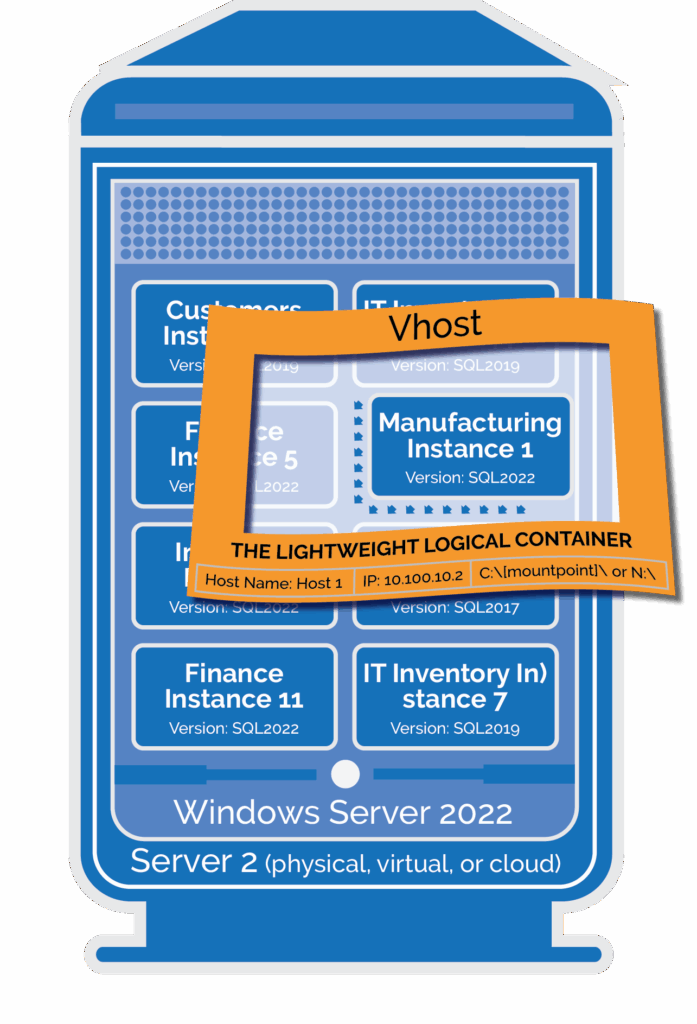
This logical, host-based abstraction is called a “Vhost.” A Vhost is a near-weightless wrapper with a network name and an IP address that can be easily unbound from one host and bound to another. Vhost technology:
- Allows instances to run on the local OS and application install—no OS weight and no boot time required (just the time for the local application or container to start)
- Supports native disk formats (NTFS,ext4,xfs), ensuring data and logs are consistently presented wherever the Vhost is active
- Easily and consistently transfers instances and containers between hosts while persisting data
How to Use Vhosts to Unlock 8-15x SQL Server Consolidation
You know the job of the Vhost now. It decouples application instances and containers from any underlying infrastructure for easy portability. Now, how do you leverage this technology to shrink your OS footprint by 8-15x while maintaining high availability and performance?
Step-by-Step Consolidation Process
Step 1: Create Vhosts – It’s easy to provision a logical host. All you need is a host name and an IP address and the Vhost is active.
Step 2: Assign workloads – Using our simple, drag-and-drop interface, applications and containers can be assigned to be managed by the Vhost, along with persistent disk resources.
Step 3: Consolidate – Once your workloads are encapsulated by the Vhosts you created, you can safely stack multiple Vhosts—with dependency coordination—on a single server. The applications/containers remain standalone while leveraging the local OS and application install.
Step 4: Eliminate unneeded OSes – Once you’ve achieved the desired stacking ratios and finalized your HA framework, you can decommission unused hosts that are not needed as potential failover targets.
Ensuring High Availability for Stacked SQL Server Workloads
DxEnterprise ensures that stacking instances and containers in this manner is a safe and reliable practice by providing intelligent failover automation in the case of issues or outages. If a workload is disrupted or falling short of its pre-configured performance SLA, DxE’s intelligent failover engine will:
- Identify an alternative host (physical, virtual, or cloud) within your HA clustering framework that provides the best execution venue (BEV) for the workload to run performantly
- Automatically failover and rehost the individual instance on the new host in seconds (the speed of an application stop-start)
NOTE: This automatic failover capability can even be easily configured for instances and containers, and even across multi-subnet geo-clusters.
While 8-15x represents the average consolidation factor achieved by our customers, some companies have even exceeded these numbers. E.g. Asante Health System was able to safely consolidate 15-20 instances per server to reverse the unsustainable VM sprawl their IT team was dealing with.
Cut SQL Server Licensing Costs by 30-60%
DxEnterprise-driven consolidation isn’t just about operational simplicity—it directly translates to licensing cost reductions, especially for Windows Server environments. Fewer Windows Server hosts = Lower Windows Server licensing costs.
Consolidation isn’t the only contributor to the 30-60% cost savings made possible with DxE though. DxEnterprise also helps bypass licensing limitations that Microsoft has put in place for Windows clusters and virtualization:
Microsoft Limitation: Using native features, SQL Server only supports a two-node cluster when using SQL Server Standard Edition, requiring SQL Server Enterprise Edition as well as Windows Server Enterprise for any clusters with three or more nodes.
Solution: DxE allows you to use any edition of SQL Server, from Express to Enterprise, in a cluster containing as many nodes as you wish—all while maintaining full license compliance. This flexibility allows you to choose SQL Server Enterprise Edition for only those instances that require its capabilities, maximizing licensing efficiency without compromising functionality.
Reach Near-Zero Total Downtime with Simplified Modernization
Many of our customers come for the consolidation and cost savings but stay for the operational simplicity that DxEnterprise provides—streamlined failover, patching, and upgrades.
Fully Automatic Failover to Minimize Unplanned Downtime
DxEnterprise aims to eliminate the need for manual failover intervention by your database administration team. It provides intelligent failover automation to keep workloads running at their respective BEVs:
- If a server outage is detected
- If a pre-configured SLA is not being
- For both instances and containers
NOTE: DxEnterprise provides the industry’s only solution for fully automatic failover for SQL Server Availability Groups in Kubernetes.
Simplified SQL Server Patching/Upgrades for Near-Zero Planned Downtime
DxEnterprise differentiates itself from other industry solutions by putting a huge engineering emphasis on reducing planned downtime for SQL Server users as well.
The key to solving the patch/update headache is the workload portability provided by InstanceMobility. It allows you to:
- Keep managed Vhost applications running on any server you choose to allow you to patch non-active nodes
- Rehost applications and containers on the newly updated node with a simple stop-restart
When utilizing this InstanceMobility-driven modernization approach:
- Managed applications never have to wait for a server to reboot, so applying a patch is minimally intrusive to any running application.
- Risk is minimized since the current active node is untouched, and if necessary, you can facilitate immediate failback to the known-good host.
- Planned downtime is now the speed of an application stop and restart.
This has huge implications for DBA teams—unlocking the ability to complete modernization tasks during normal business hours and dramatically reducing after-hours maintenance.
You can learn more about what the SQL Server upgrade process looks like with DxEnterprise on the DH2i Support Site.
Try DxEnterprise Free: Experience the Difference
Are you ready to simplify your SQL Server environment, cut costs, and eliminate downtime? Put InstanceMobility and Vhost technology to work in your own environment and start a free trial of DxEnterprise. It won’t take long to understand how your organization can unlock:
- An 8-15x reduction in OSes under management
- 30-60% savings on SQL Server and Windows Server licensing costs
- Minimized planned and unplanned downtime with simplified modernization